It turns out Zidoo changed design in 2018...
Those 2017 pictures are with DDR4 ram, but my "China Version" has DDR3 ram, exactly same chip as Beelink GS1.
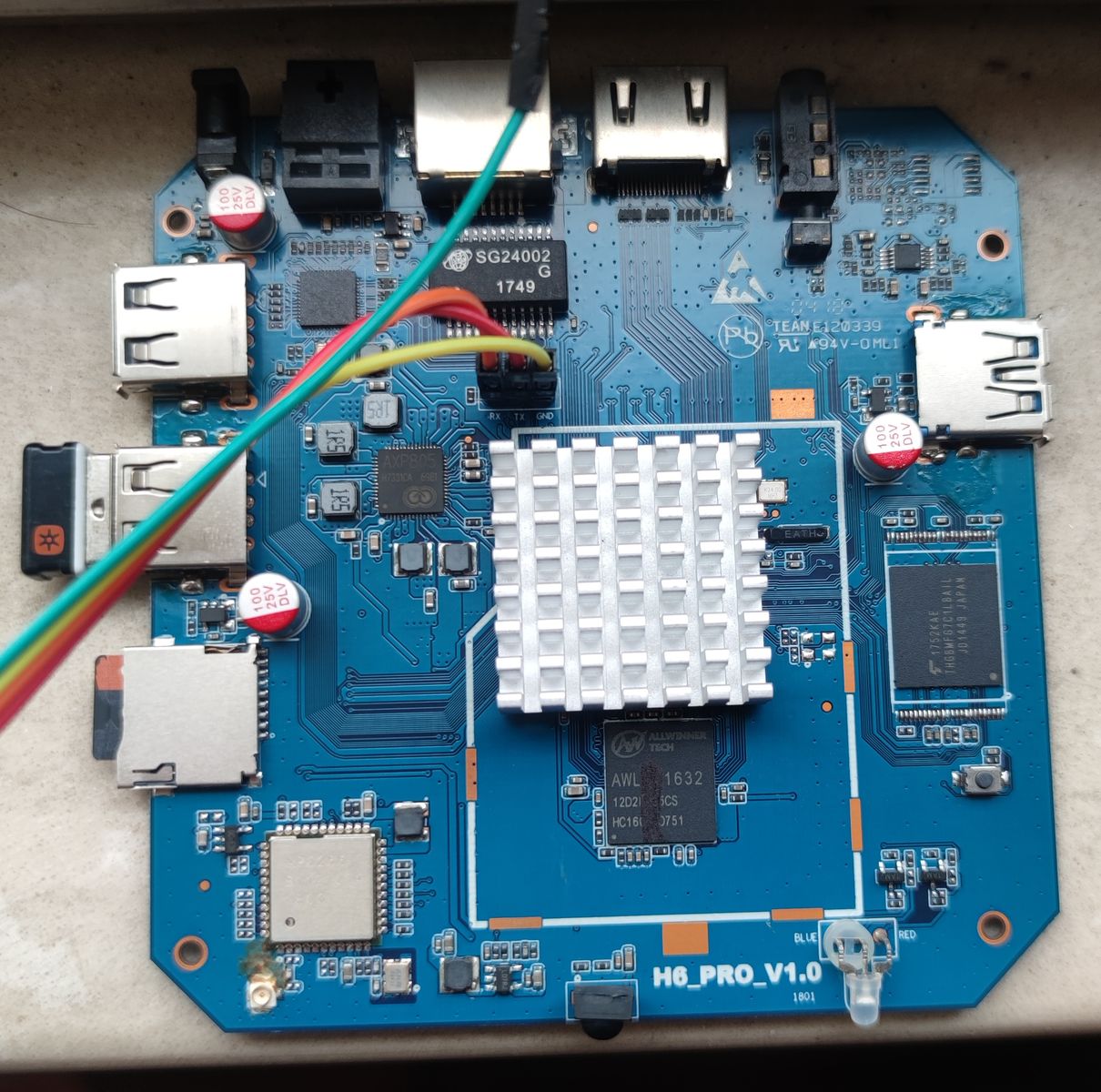
UART is already popped out so I saved some soldering work. BTW, TX/RX are actually reversed.
This is the uart log:
[295]HELLO! BOOT0 is starting!
[298]sbrom commit : fe74891e7937253e1c219626615607da4ad37a02
[315]PMU: AXP806
[317]vdd-sys vol:980mv
[320]set pll start
[322]set pll end
[324]try to probe rtc region
[326]rtc[0] value = 0x00000000
[329]rtc[1] value = 0x00000000
[332]rtc[2] value = 0x00000000
[335]rtc[3] value = 0x00000000
[338]rtc[4] value = 0x00000000
[341]rtc[5] value = 0x00000000
[344]flag=0x00000000
[346]DRAM VERSION IS V2_5
[349]PMU:Set DDR Vol 1200mV OK.
[352]DRAM CLK =912 MHZ
[354]DRAM Type =7 (3:DDR3,4:DDR4,6:LPDDR2,7:LPDDR3)
[359]DRAM zq value: 003b3bfb
[365]IPRD=00580058--PGCR0=00000f5d--PLL=b0004b00
[370]DRAM SIZE =2048 M,para1 = 000030fa,para2 = 08001000
[378]DRAM simple test OK.
[381]init dram ok, size=2048M
[384]init heap
[385][mmc]: mmc driver ver 2017-03-14 13:56
[390][mmc]: mmc 2 bias 00000004
[398][mmc]: ***Try MMC card 2***
[419][mmc]: MMC 5.0
[421][mmc]: HSDDR52/DDR50 4 bit
[424][mmc]: 50000000 Hz
[427][mmc]: 15028 MB
[429][mmc]: ***SD/MMC 2 init OK!!!***
[553]read toc1 from emmc 32800 sector
[556]OLD version: 0.0
[558]NEW version: 0.0
[561]probe root certif
[566]enter the two key ladder pk check!
[571]certif valid: the root key is valid
[817]find scp key stored in root certif
[828]set arisc reset to de-assert state
[950]find monitor key stored in root certif
[955]ready to run monitor
[1078]find optee key stored in root certif
[1086]ready to run optee
[1209]find boot key stored in root certif
[1334]find recovery key stored in root certif
[1460]find u-boot key stored in root certif
[1482]ready to run u-boot
[1487]sbromsw_toc1_traverse find out all items
[1491]monitor entry=0x48000000
[1494]uboot entry=0x4a000000
[1497]optee entry=0x48600000
[1500]0xffffffff 0xffffffff
[1503]0xff18ffff 0xffffffff
[1506]0xff0e14ff 0xffffffff
[1508]0x1718ffff 0xffffff18
[1511]0x0e22ffff 0xffffffff
[1514]0x1a1affff 0xffffffff
[1519]drm_region_ofs = 944, bitmap_ofs = 241664, bitmap_write_len = 20480
[1526]storage_type=2
[1528]dram = 2048 M
INFO: Configuring SPC Controller
NOTICE: BL3-1: v1.0(debug):7408d88
NOTICE: BL3-1: Built : 20:42:28, Aug 29 2017
NOTICE: BL3-1 commit: 7408d88f80cb14038350a8f55a280fd0c4caf626
INFO: BL3-1: Initializing runtime services
NOTICE: secure os exist
INFO: BL3-1: Initializing BL3-2
INFO: BL3-1: Preparing for EL3 exit to normal world
INFO: BL3-1: Next image address = 0x4a000000
INFO: BL3-1: Next image spsr = 0x1d3
U-Boot 2014.07 (Sep 27 2017 - 11:02:27) Allwinner Technology
uboot commit : f1305b8180811ad316c35a2fcc8341c2b12c34fe
secure enable bit: 1
secure mode: with secureos
I2C: ready
[1.585]pmbus: ready
u0:f8441b39
[1.585][ARISC] :arisc initialize
[1.609][ARISC] :arisc para ok
[SCP] :sunxi-arisc driver begin startup 2
[SCP] :arisc version: [v0.3.13]
[SCP] :sunxi-arisc driver v1.10 is starting
[1.623][ARISC] :sunxi-arisc driver startup succeeded
[1.624]PMU: AXP806
[1.624]PMU: AXP806 found
[1.624]bat_vol=0, ratio=0
axp=axp806, supply=bldo2, vol=1800
axp=, supply=, vol=0
[1.628]set power on vol to default
[1.628]dcdca_vol = 1000, onoff=1
[1.632]aldo2_vol = 3300, onoff=1
[1.636]find power_sply to end
[1.640]dcdca_vol = 1100, onoff=1
[1.641]PMU: cpux 888 Mhz,AXI=296 Mhz
PLL6=600 Mhz,AHB1=200 Mhz, APB1=150Mhz MBus=400Mhz
DRAM: 2 GiB
[1.643]fdt addr: 0xb6ccef20
[1.643]gd->fdt_size: 0x187a0
Relocation Offset is: 75d77000
gic: sec monitor mode
[box standby] read rtc = 0x0
[box standby] start_type = 0x1
[box standby] to kernel
ir boot recovery not used
[1.753][key recovery] no key press.
[1.753]power on cpu1
[1.753][cpu1]task entry
[1.753][cpu1]PowerBus = 0( 2:vBus 3:acBus other: not exist)
[1.753][cpu1]no battery exist
[1.753]start
[cpu1]drv_disp_init
[cpu1]init_clocks: finish init_clocks.
[1.763]power on cpu2
workmode = 0,storage type = 2
[1.763]MMC: 2
[1.763][mmc]: mmc driver ver 2017-09-4 10:12:00
[1.763][cpu2]task entry
[1.764][cpu1]HDMI 2.0 driver init start!
[1.765][cpu2]ready to work
[1.766][mmc]: get sdc_ex_dly_used 2, use auto tuning sdly
[cpu1]__clk_enable: clk is null.
[1.776][mmc]: card2 io is 1.8V.
[1.779][cpu1]hdmi cec clk enable failed!
[1.782][mmc]: get sdc2 sdc_tm4_hs200_max_freq 150.
[1.785][cpu1]enable ddc_scl pin
[1.790][mmc]: get sdc2 sdc_tm4_hs400_max_freq 100.
[1.793][cpu1]enable ddc_sda pin
SUNXI SD/MMC: 2[1.800][cpu1]enable hmid cec pin
[1.810][mmc]: media type 0x8000000
[1.810][mmc]: Try MMC card 2
[1.811][cpu2]cpu 2 enter wfi mode
[1.829][mmc]: host caps: 0x1ef
[1.829][mmc]: MID 000011 PSN 63cb2e71
[1.829][mmc]: PNM 016G70 -- 0x30-31-36-47-37
[1.829][mmc]: PRV 0.0
[1.829][mmc]: MDT m-12 y-2017
[1.829][mmc]: MMC v5.0
[1.830][mmc]: bus_width : 8 bit
[1.833][mmc]: user capacity : 15028 MB
[1.837][mmc]: SD/MMC 2 init OK!!!
[1.841][mmc]: Best spd md: 4-HS400, freq: 3-100000000
[1.845][mmc]: EOL Info(Rev blks): Normal
[1.848][mmc]: Wear out(type A): [1.851][mmc]: 0%-10% life time used
[1.854][mmc]: Wear out(type B): [1.857][mmc]: Not defined
[1.859][mmc]: End mmc_init_boot
[1.862]sunxi flash init ok
used mbr [0], count = 15
[1.867]try to burn key
read item0 copy0
the secure storage item0 copy0 is good
no item name key_burned_flag in the map
sunxi storage read fail
sunxi secure storage has no flag
[1.883]usb burn from boot
delay time 0
[1.892]usb prepare ok
[cpu1]pwm_request: reg = 0x300a000. pwm = 1.
[cpu1]request pwm success, pwm = 1.
[cpu1]speed=200000, slave=16
[cpu1]drv_disp_init finish
[cpu1]name in map hdcpkey
[cpu1]the secure storage item1 copy0 is good
[cpu1]len=4096
[cpu1]name=hdcpkey
[cpu1]len=288
[cpu1]encrypt=1
[cpu1]write_protect=0
[cpu1]******************
[cpu1]push hdcp key finish!
[cpu1]get format[40a] for type[4]
[cpu1]get format[20b] for type[2]
[cpu1]main-hpd:count=1,sel=0,type=4
[cpu1]invalid display config
[cpu1]edid all null
[cpu1]save_int_to_kernel disp.tv_vdid(0x0) code:<no error>
[2.137][cpu1][HDMI2.0]CEA VIC=16: [2.140][cpu1]1920x1080p[2.142][cpu1]@60 Hz [2.144][cpu1]16:9, [2.145][cpu1]0-bpp [2.147][cpu1]YCbCr-444
[2.149][cpu1]BT709
[2.262][cpu1]attched ok, mgr0<-->dev0
[2.262][cpu1]type,mode,fmt,bits,eotf,cs=4,10,yuv444,undef,0,257
[cpu1]save_int_to_kernel disp.boot_disp(0x40a) code:<no error>
[cpu1]save_int_to_kernel disp.init_disp(0x20b0000) code:<no error>
[cpu1]invalid display config
[cpu1]save disp device failed
[cpu1]size=0x384000, ram_size=0x80000000, FRAME_BUFFER_SIZE=0x1000000
[2.272]end
[cpu1]advert_enable not set
[cpu1]save_string_to_kernel disp.boot_fb0(bf000000,500,2d0,20,1400,0,0,500,2d0). ret-code:<no error>
[2.284][cpu1]boot logo from boot_package/toc1 item display ok
[2.340][cpu1]cpu 1 enter wfi mode
[2.693]overtime
[2.696]do_burn_from_boot usb : no usb exist
--------fastboot partitions--------
-total partitions:15-
-name- -start- -size-
bootloader : 1000000 1000000
env : 2000000 1000000
boot : 3000000 2000000
system : 5000000 60000000
verity_block: 65000000 1000000
misc : 66000000 1000000
recovery : 67000000 2000000
sysrecovery : 69000000 60000000
private : c9000000 1000000
alog : ca000000 4000000
Reserve0 : ce000000 1000000
Reserve1 : cf000000 2000000
Reserve2 : d1000000 1000000
cache : d2000000 30000000
UDISK : 2000000 0
-----------------------------------
not suppert programmer
base bootcmd=run setargs_nand boot_normal
bootcmd set setargs_mmc
misc partition found
[2.755]to be run cmd=run setargs_mmc boot_normal
mac string is 00:00:00:00:00:00
no item name wifi_mac in the map
sunxi storage read fail
no item name bt_mac in the map
sunxi storage read fail
no item name selinux in the map
sunxi storage read fail
no item name specialstr in the map
sunxi storage read fail
check user data form private
updataed mac = 80:0A:80:52:47:C4
[2.788][mmc]: hsddr 2-50000000
[2.790][mmc]: hs200 4-150000000
[2.793][mmc]: hs400 3-100000000
[2.796][mmc]: get max-frequency ok 150000000 Hz
[2.800][mmc]: 0 0 0: 0 0 0
[2.802][mmc]: get max-frequency ok 100000000 Hz
[2.810]drm_base=0xbb000000
[2.810]drm_size=0x5000000
[2.812]update dtb dram start
[2.815]update dtb dram end
serial is: 0c000141091e3c2c058b
name in map widevine
the secure storage item2 copy0 is good
len=4096
name=widevine
len=128
encrypt=1
write_protect=1
******************
[2.832]key install finish
Net: phy_mode=rgmii, phy_interface=6
eth0
Warning: failed to set MAC address
[2.845]inter uboot shell
Hit any key to stop autoboot: 0
[2.847]read partition: boot or recovery
[2.958]sunxi flash read :offset 3000000, 18272099 bytes OK
Kernel load addr 0x40080000 size 13490 KiB
Kernel command line: selinux=1 androidboot.selinux=enforcing cma=64M, use it to update bootargs
RAM disk load addr 0x41000000 size 3330 KiB
total_len=17225728
task_id is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
task_id is 0
task_id is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
xx is 0
[3.253]ready to boot
[3.253]check cpu power status
[3.253]cpu2 has poweroff
[3.253]cpu1 has poweroff
[3.257]prepare for kernel
[3.257]check cpu power status
[3.257]cpu2 has poweroff
[3.257]cpu1 has poweroff
[3.257][mmc]: mmc exit start
[3.280][mmc]: mmc 2 exit ok
[3.280]
Starting kernel ...
INFO: BL3-1: Next image address = 0x40080000
INFO: BL3-1: Next image spsr = 0x3c5
[ 0.000000] Initializing cgroup subsys cpu
[ 0.000000] Initializing cgroup subsys cpuacct
[ 0.000000] Linux version 3.10.65 (hepeng@ZidooServer) (gcc version 4.9.3 20150113 (prerelease) (Linaro GCC 4.9-2015.01-3) ) #1 SMP PREEMPT Fri Jan 12 15:58:57 CST 2018
[ 0.000000] CPU: AArch64 Processor [410fd034] revision 4
[ 0.000000] Machine: sun50iw6
[ 0.000000] bootconsole [earlycon0] enabled
petrel-p1:/ $
Display More
Insert LE tf card will get me same uart output and still boot into Android on internal emmc at /dev/block/mmcblk0.
The LE card is recognized by the stock firmware at /dev/block/mmcblk1. It is not mounted in the console display printed by "df -h", but can be seen in Android file manager.
I am going to create a card with phoenixcard and see what's the magic there..
stock firmware image tf card written by phoenixcard will get this boot message:
[337]HELLO! BOOT0 is starting!
[340]sbrom commit : fe74891e7937253e1c219626615607da4ad37a02
[357]PMU: AXP806
[359]vdd-sys vol:980mv
[362]set pll start
[364]set pll end
[366]try to probe rtc region
[368]rtc[0] value = 0x00000000
[371]rtc[1] value = 0x00000000
[374]rtc[2] value = 0x00000000
[377]rtc[3] value = 0x00000000
[380]rtc[4] value = 0x00000000
[383]rtc[5] value = 0x00000000
[386]flag=0x00000000
[388]DRAM VERSION IS V2_5
[391]PMU:Set DDR Vol 1200mV OK.
[394]PMU:Set DDR Vol 1200mV OK.
[412]DRAM CLK =912 MHZ
[414]DRAM Type =7 (3:DDR3,4:DDR4,6:LPDDR2,7:LPDDR3)
[419]DRAM zq value: 003b3bfb
[425]IPRD=00590059--PGCR0=00000f5d--PLL=b0004b00
[430]DRAM SIZE =2048 M,para1 = 000030fa,para2 = 08001000
[438]DRAM simple test OK.
[441]init dram ok, size=2048M
[444]init heap
[445][mmc]: mmc driver ver 2017-03-14 13:56
[449][mmc]: sdc0 spd mode error, 2
[453][mmc]: mmc 0 bias 00000000
[461][mmc]: Wrong media type 0x00000000
[465][mmc]: ***Try SD card 0***
[474][mmc]: HSSDR52/SDR25 4 bit
[477][mmc]: 50000000 Hz
[480][mmc]: 3768 MB
[482][mmc]: ***SD/MMC 0 init OK!!!***
[668]read toc1 from emmc 32800 sector
Display More
It gives "sdc0 spd mode error, 2", then turn to boot from mmc0(tf card) instead of mmc2(emmc).
@jernej Any clue?

